What is penetration testing and vulnerability assessment? The first thing you do after setting up the server and network system for your company is to test the network security vulnerabilities. As the person in-charge of the IT infrastructure, be it in a school, university, public library, web hosting companies, enterprise server or small business computers, penetrationstest is always a must, to perform penetration tests and security assessments for all the networks you will need these free penetration testing tools.
Continue ➤ 6 Free Anti NSA Anonymity Tools – Stops Tracking And Hides IP Address
How to do penetration testing? These are bootable Linux operating systems, they are “security-focused”, which means that the project is devoted to increasing the security as a major goal. It is not possible to be 100% secure, but with the right tools, certain security holes can be disabled. That’s where Pen-testing comes handy with its use of ethical hacking techniques. Below are some of the best penetration testing companies (Subscribe to their service) and Linux OS (DIY).
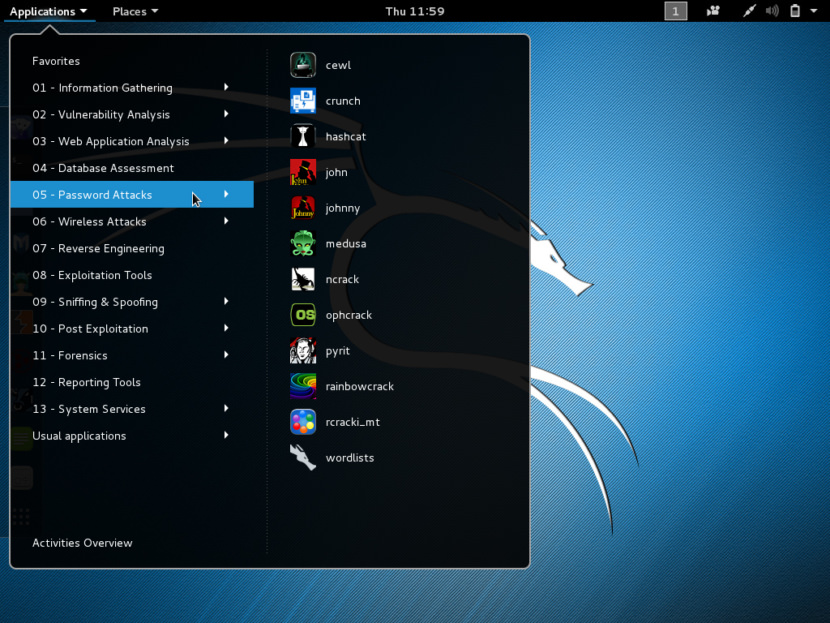
1. Kali Linux
Kali Linux is the most advanced penetration testing platform ever made. Available in 32 bit, 64 bit, and ARM flavors, as well as a number of specialized builds for many popular hardware platforms. It is the only provider of true performance-based penetration testing training for over a decade. Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing, originally forked from Backtrack Linux by the Offensive Security team.
Kali Linux is preinstalled with numerous penetration-testing programs, including Small Nmap iconNmap (a port scanner), Small Wireshark iconWireshark (a packet analyzer), Small John the Ripper iconJohn the Ripper (a password cracker), and Small Aircrack-ng iconAircrack-ng (a software suite for penetration-testing wireless LANs).
- Wireless Attacks
- Vulnerability Analysis
- Information Gathering
- Forensics Tools
- Exploitation Tools
- Stress Testing
- Network security assessment
- Sniffing & Spoofing
- Password Attacks Test
- Hardware Hacking
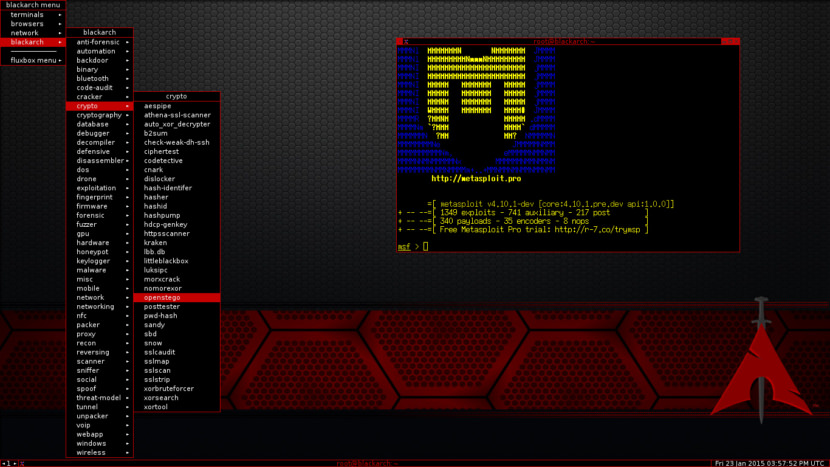
2. BlackArch
BlackArch Linux is an Arch Linux-based penetration testing distribution for penetration testers and security researchers. The repository contains 1632 tools. You can install tools individually or in groups. BlackArch Linux is compatible with existing Arch installs. The repository contains 1218 tools. You can install tools individually or in groups. BlackArch Linux is compatible with existing Arch installs.
- A network scanner for discovery and security.
- WEP, WPA wifi cracker for wireless penetration testing
- Brute force attack against Wifi Protected Setup
- A collection of traffic analysis tools developed by the CERT NetSA to facilitate security analysis of large networks.
- Dumps system memory to stdout, skipping over holes in memory maps.
- WLAN penetration tool
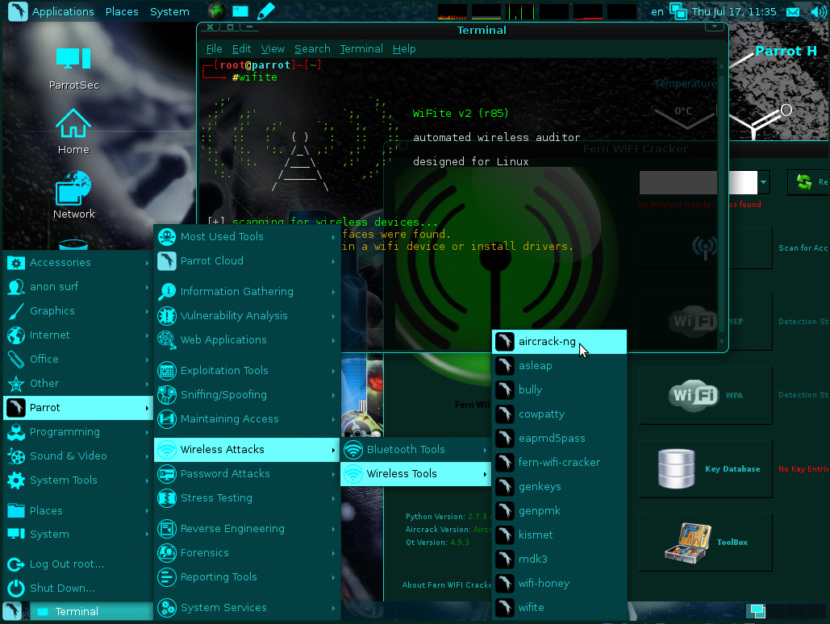
3. Parrot Security
Parrot Security is a security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital forensics experts, but it also includes all you need to develop your own softwares or protect your privacy with anonymity and crypto tools. Parrot Security includes a full arsenal of security oriented tools to perform penetration tests, security audits and more. With a Parrot usb drive in your pocket you will always be sure to have all you need with you.
- Cloud Pentesting – Parrot Cloud is a special edition of their OS specifically designed for servers, it consists of a lightweight parrot system without graphic interfaces, wireless and forensic tools and any other tools that can be considered useless in a remote-controlled virtual environment.
- Digital Forensics – Parrot Security is developed in collaboration with Caine, one of the most important GNU/Linux distributions in the Digital Forensics world – One of their purposes is to provide the best forensics environment ever seen in a security distro, in fact the entire system is hardened to not perform device automounts and to provide all the tools needed to do forensic acquisitions and evidence identifications in a safe comprehensive and portable virtual lab.
- Cryptography – Parrot includes many cryptographic softwares. which are extremely useful when it comes to protecting your confidential data and defending your privacy. Parrot includes several cryptographic front-ends to work both with symmetric and asymmetric encryption, in fact it natively supports volumes encryption with LUKS, TrueCrypt, VeraCrypt and the hidden TrueCrypt/VeraCrypt volumes with nested algorithms support.
4. BackBox
BackBox is more than an operating system, it is a Free Open Source Community project with the aim to promote the culture of security in the IT environment and give its contribution to make it better and safer. All this using exclusively Free Open Source Software by demonstrating the potential and power of the community. If you’d like to know more feel free to navigate to their website and get in touch with us. Penetration Tools List
- Information Gathering
- Vulnerability Assessment
- Web Attack
- Exploitation Testing
- Privilege Escalation
- Password Attack
- Social Engineering
- Man In The Middle Attack
- Stress Testing
- Wireless WEP WAP and WAP2 Attack
- Maintaining Access
- Forensics Tools
- Reverse Engineering
- Malware Analysis
- Covering Track
5. Cyborg Linux
[ Discontinued ] Cyborg Linux – World’s Most Advanced Penetration Testing Distro. The most advanced, powerful and yet beautiful penetration testing distribution ever created.Lined up with the ultimate collection of tools for pro Ethical Hackers and Cyber Security Experts. Simplify security in your IT infrastructure with Cyborg. Its real strength comes from the understanding that a tester requires a strong and efficient system that benefits from a strong selection of tools, integrated with a stable linux environment.
- xploitation Toolkit – Toolkit to test the integrity of your IT Infrastructure.Best exploit of for best results
- Stress Testing – Determine the amount of stress your computer, network, program or device can bear.
- Reverse Engineering – Reversing the core code for the analysis by going backwards through the development cycle.
- Forensics – Uncover the Digital evidence. Investigate them and interpreting electronic data for use in a court of law.
- Mobile Security – Penetrate the mobile security and fix the vulnerabilities of it . Mobile Security covers every known platform for smartphones.
- Wireless Security – Secure your wireless world. Cyborg have top level tools to test your security.






Kali and back box always one of my favorites.
Informative blog about Linux OS for penetration testing. Apart from this, I have read hacker combat blog, They are given some interesting details about Web App Pen Testing Checklist & How it is Performed and Types.
Nice list. I use Kali at the moment.
BlackBSD the best one